Resolving an AuthorizationPermissionMismatch from the Azure File Copy v4 Task in Azure Pipelines
I was setting up a new Azure Pipeline today to deploy a Blazor Web Assembly application to a Static Website in Azure Storage. Despite authorising the service connection in Azure Pipelines to have access to the target storage account, I was encountering a AuthorizationPermissionMismatch error when the task executed. I suspected there was an issue with the Service Principal in Azure AD, but it took a little digging around to find the solution. Hopefully this saves some of you some time in the future.
The problem
The Azure File Copy task was reporting the following.
INFO: Authentication failed, it is either not correct, or expired, or does not have the correct permission -> github.com/Azure/azure-storage-blob-go/azblob.newStorageError, /home/vsts/go/pkg/mod/github.com/!azure/azure-storage-blob-go@v0.7.0/azblob/zc_storage_error.go:42
===== RESPONSE ERROR (ServiceCode=AuthorizationPermissionMismatch) =====
Description=This request is not authorized to perform this operation using this permission.
RequestId:217f1b71-401e-002e-5950-75bf49000000
Time:2020-08-18T11:14:03.5029669Z, Details:
Code: AuthorizationPermissionMismatch
PUT REDACTED
Authorization: REDACTED
Content-Length: [7156326]
User-Agent: [TFS_useragent AzCopy/10.3.3 Azure-Storage/0.7 (go1.13; Windows_NT)]
X-Ms-Blob-Cache-Control: []
X-Ms-Blob-Content-Disposition: []
X-Ms-Blob-Content-Encoding: []
X-Ms-Blob-Content-Language: []
X-Ms-Blob-Content-Md5: []
X-Ms-Blob-Content-Type: [application/x-zip-compressed]
X-Ms-Blob-Type: [BlockBlob]
X-Ms-Client-Request-Id: [f5443617-bb78-4bf5-595f-1f1ced4efbee]
X-Ms-Version: [2018-03-28]
--------------------------------------------------------------------------------
RESPONSE Status: 403 This request is not authorized to perform this operation using this permission.
Content-Length: [279]
Content-Type: [application/xml]
Date: [Tue, 18 Aug 2020 11:14:03 GMT]
Server: [Windows-Azure-Blob/1.0 Microsoft-HTTPAPI/2.0]
X-Ms-Error-Code: [AuthorizationPermissionMismatch]
X-Ms-Request-Id: [217f1b71-401e-002e-5950-75bf49000000]
X-Ms-Version: [2018-03-28]
The fact that I was getting a 403 and the logs were reporting an AuthorizationPermissionMismatch pointed towards some type of missing role or permission, but which one? Buried deep in this Github issue (on 2 July 2020) @asranja responded to a commenter that from v4 of the Azure File Copy task the Service Principal needs to have the Storage Blob Data Contributor role assignment.
As an aside, if I’d read the manual correctly, I would have known this.
Assigning the Storage Blob Contributor role to the Service Principal
Assuming you have the relevant access to the Azure subscription, resource group and storage account, you can add the role assignment easily enough through the Azure portal.
- Login to the Azure portal
- Find your target storage account and open up its blade.
- Select Access Control (IAM) from the left pane.
- Click “Add” from the menu bar.
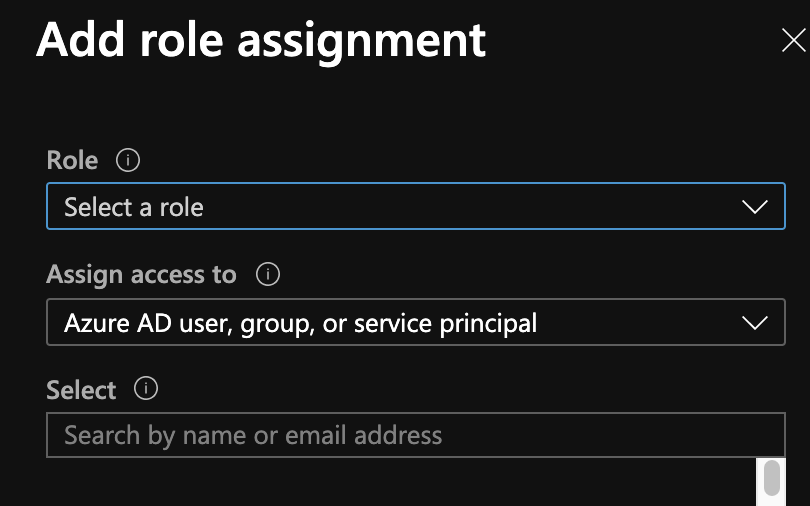
- The Add role assignment panel will appear.
- Choose Storage Blob Data Contributor from the Role dropdown.
- Leave the Assign access to dropdown set to Azure AD user, group or service principal.
- You’ll probably need to search for the service principal if Azure Pipelines created it for you via a service connection. What worked for me was to enter the name of my Azure DevOps organisation. I was then able to select the appropriate service principal from the list.
- Click Save to apply the role assignment.
That’s all there was to it. When I re-queued the pipeline my Blazor app was deployed to the $web container in the Storage Account without issue.
